L2TPv3 – A wormhole through your L3 network.
Using L2 tunnel protocol version 3, you can accomplish what so many scientists are working on. A Wormhole!
Granted, this wormhole is just through your L3 network, so it might not raise as many eyebrows, but its still a nifty tool in your toolbox.
This will be a fairly short post, but it does give you the ability to see how this works and what you can use it for.
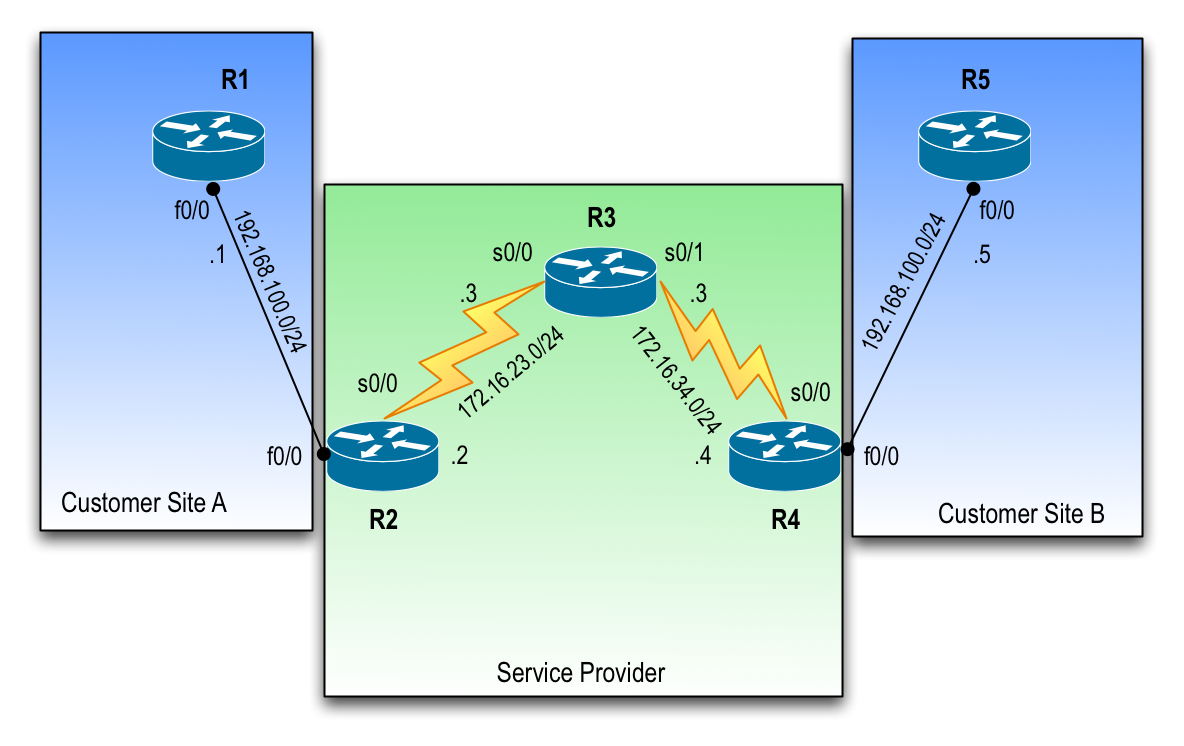
Lets take the following topology into account:
Assume the following things regarding this topology:
1) Your wish to extend the L2 segment present on both site A and site B through the Service Provider network.
2) The Service provider can be a “real” service provider, or simply your own campus network.
So what does L2TPv3 provide for you? — Well, all it does it to take your L2 data, encapsulate it, transfer it through the L3 network, decapsulate it and pass it on as the original L2 data.
Lets take a look at some of the configuration. First off, i have setup the “Service Provider” with RIP version 2, probably not what you want to do in real life, but it serves its purpose just fine. So R2, R3 and R4 have reachability to the 2 L3 subnets thats in between them.
The place where you want to configure this, is on the inbound side of the L3 device connecting to your service provider. In this example, that means on R2 and R4 on their respective FastEthernet interfaces. It is not nessecary to have any L3 information configured on these interfaces, and in fact i dont:
R2#sh run int f0/0 Building configuration... Current configuration : 114 bytes ! interface FastEthernet0/0 no ip address duplex auto speed auto end
In order to get L2TPv3 working, we need to setup a pseudowire class. A pseudowire class is like a template, containing information required later on in order to establish the connection between the routers.
These pseudowire classes dont require much information, basically only the encapsulation type as well as the interface to use for the encapsulation and passing of information. Lets see the configuration on R2:
pseudowire-class MYPW encapsulation l2tpv3 ip local interface Serial0/0
Not much to it right. We want to use the latest and greatest version 3 of L2TP. We also specify that the serial interface will be used for the sourcing of this tunnel. You could be using loopback interfaces for this type of thing, but for this example it doesnt really matter much.
Next up is applying this thing to your interface. Remember, its the SP interface towards you as the customer that needs to be changed. R2 f0/0 and R4 f0/0 in our case:
R2(config-if)# xconnect 172.16.34.4 1000 pw-class MYPW
And on R4:
R4(config-if)# xconnect 172.16.23.2 1000 pw-class MYPW
Now lets do some verification to see that our tunnel has been established:
On R2:
R2#sh l2tp tunnel
L2TP Tunnel Information Total tunnels 1 sessions 1
LocTunID RemTunID Remote Name State Remote Address Sessn L2TP Class/
Count VPDN Group
5042 56821 R4 est 172.16.34.4 1 l2tp_default_cl
And on R4:
R4#sh l2tun
L2TP Tunnel and Session Information Total tunnels 1 sessions 1
LocTunID RemTunID Remote Name State Remote Address Sessn L2TP Class/
Count VPDN Group
56821 5042 R2 est 172.16.23.2 1 l2tp_default_cl
LocID RemID TunID Username, Intf/ State Last Chg Uniq ID
Vcid, Circuit
41300 7194 56821 1000, Fa0/0 est 00:18:02 1
All great, we can see that the tunnels has been established. More importantly can we ping through our network now:
R1#ping 192.168.100.5 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.100.5, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 12/17/24 ms R1#sh arp Protocol Address Age (min) Hardware Addr Type Interface Internet 192.168.100.1 - c200.0fdf.0000 ARPA FastEthernet0/0 Internet 192.168.100.5 30 c204.0fe2.0000 ARPA FastEthernet0/0
Success! You are now the mad scientist having created the wormhole.
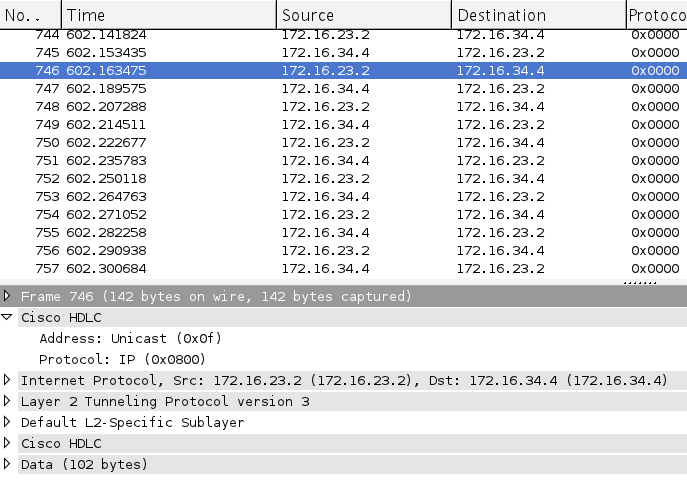
Final thing i want to let you know of, is the impact of doing this. Below is a screenshot of what a capture looks like:
As you can see, its not without its penalty of doing this sort of thing. You have the entire L2 data being encapsulated into a new L2TPv3 header, which by itself takes up some space, and then you have your regular IP header in order to move the data across the L3 network.
Having taken this into consideration, L2TPv3 might still be a good tool in your toolbox, when you need L2 connectivity across a L3 network.
I hope this mini-post was useful to you. Until next time!