SVTI's Explained
The Concept:
In legacy site to site (S2S) VPN’s we are used to defining crypto maps and applying them to a physical interface. However, since these does not utilize GRE, you have no way of supporting multicast and routing protocols. This leads to having to define “interesting” traffic using ACL’s. Something which is clearly not scalable.
Instead, we can now use Static Virtual Tunnel Interface’s, which does not use GRE either, but it does support both multicast and routing protocols. Along with that, since we are using a new logical interface, things such as ACL’s and QoS is fully supported.
When looking at the encapsulation, all you will see on the link is ESP (protocol 50).
The Use Case(s):
I would argue that any new implementation of S2S (P2P) VPN, would benefit from moving towards SVTI’s. Running an IGP on top of your tunnel is far more scalable and flexible than having to define ACL/Mirror ACL on each side of the connection.
If you are a QoS kind of a guy/girl, then that alone should be enough of a reason to move to SVTI’s.
Be aware that since you are using up logical interfaces and you might be (probably) running IGP on top (as opposed to static routes) the limitation to using SVTI’s, will most likely be the amount of routing adjacencies and/or tunnel interfaces.
The Configuration(s):
I have listed 2 types of configurations. One using IKEv1 and one using IKEv2.
The topology is simple:
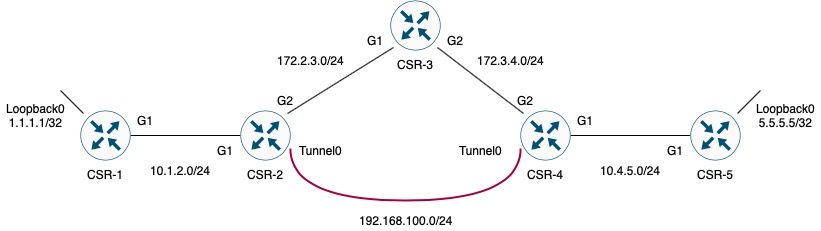
Note that we are running OSPF Area 0 on all links except those going from CSR-2 to CSR-3 and those from CSR-3 to CSR-4 as these emulate internet connections.
First up is IKEv1:
IKEv1:
CSR-2:
crypto keyring MYKEYRING
pre-shared-key address 0.0.0.0 0.0.0.0 key cisco
!
!
crypto isakmp policy 10
encryption 3des
authentication pre-share
group 5
crypto isakmp profile MYISAKMP-PROFILE
keyring MYKEYRING
match identity address 172.3.4.4 255.255.255.255
!
!
crypto ipsec transform-set MYTS esp-3des esp-md5-hmac
mode tunnel
!
crypto ipsec profile MYIPSEC-PROFILE
set transform-set MYTS
set isakmp-profile MYISAKMP-PROFILE
!
interface Tunnel0
ip address 192.168.100.2 255.255.255.0
tunnel source GigabitEthernet2
tunnel mode ipsec ipv4
tunnel destination 172.3.4.4
tunnel protection ipsec profile MYIPSEC-PROFILEAnd CSR-4:
crypto keyring MYKEYRING
pre-shared-key address 0.0.0.0 0.0.0.0 key cisco
!
!
crypto isakmp policy 10
encryption 3des
authentication pre-share
group 5
crypto isakmp profile MYISAKMP-PROFILE
keyring MYKEYRING
match identity address 172.2.3.2 255.255.255.255
!
!
crypto ipsec transform-set MYTS esp-3des esp-md5-hmac
mode tunnel
!
crypto ipsec profile MYIPSEC-PROFILE
set transform-set MYTS
set isakmp-profile MYISAKMP-PROFILE
!
interface Tunnel0
ip address 192.168.100.4 255.255.255.0
tunnel source GigabitEthernet2
tunnel mode ipsec ipv4
tunnel destination 172.2.3.2
tunnel protection ipsec profile MYIPSEC-PROFILEon CSR-2, lets verify that we have an OSPF adjacency across the tunnel:
CSR-2#sh ip os nei
Neighbor ID Pri State Dead Time Address Interface
4.4.4.4 0 FULL/ - 00:00:38 192.168.100.4 Tunnel0
1.1.1.1 1 FULL/DR 00:00:30 10.1.2.1 GigabitEthernet1And lets check out our ISAKMP and IPsec SA’s as well:
CSR-2#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
172.2.3.2 172.3.4.4 QM_IDLE 1002 ACTIVE
IPv6 Crypto ISAKMP SA
CSR-2#sh crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 172.2.3.2
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 172.3.4.4 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 123, #pkts encrypt: 123, #pkts digest: 123
#pkts decaps: 123, #pkts decrypt: 123, #pkts verify: 123
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.2.3.2, remote crypto endpt.: 172.3.4.4
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet2
current outbound spi: 0x14A8AF8F(346599311)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xE29B1C97(3801816215)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2017, flow_id: CSR:17, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607984/2460)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x14A8AF8F(346599311)
transform: esp-3des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 2018, flow_id: CSR:18, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607987/2460)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:All looks good! - now lets verify the data connection between the loopbacks between CSR-1 and CSR-5:
CSR-1#ping 5.5.5.5 so loo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/5 msNow lets do the same exercise with IKEv2:
IKEv2:
CSR-2:
crypto ikev2 proposal MY-IKEV2-PROPOSAL
encryption 3des
integrity sha1
group 14
!
crypto ikev2 policy MY-IKEV2-POLICY
proposal MY-IKEV2-PROPOSAL
!
crypto ikev2 keyring MY-IKEV2-KEYRING
peer 172.3.4.4
address 172.3.4.4
pre-shared-key local cisco
pre-shared-key remote cisco
!
!
!
crypto ikev2 profile MY-IKEV2-PROFILE
match identity remote address 172.3.4.4 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local MY-IKEV2-KEYRING
!
!
crypto ipsec transform-set MYTS esp-3des esp-md5-hmac
mode tunnel
!
crypto ipsec profile MY-IPSEC-PROFILE
set transform-set MYTS
set ikev2-profile MY-IKEV2-PROFILE
!
interface Tunnel0
ip address 192.168.100.2 255.255.255.0
tunnel source GigabitEthernet2
tunnel mode ipsec ipv4
tunnel destination 172.3.4.4
tunnel protection ipsec profile MY-IPSEC-PROFILE
!And CSR-4:
crypto ikev2 proposal MY-IKEV2-PROPOSAL
encryption 3des
integrity sha1
group 14
!
crypto ikev2 policy MY-IKEV2-POLICY
proposal MY-IKEV2-PROPOSAL
!
crypto ikev2 keyring MY-IKEV2-KEYRING
peer 172.2.3.2
address 172.2.3.2
pre-shared-key local cisco
pre-shared-key remote cisco
!
!
!
crypto ikev2 profile MY-IKEV2-PROFILE
match identity remote address 172.2.3.2 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local MY-IKEV2-KEYRING
!
!
crypto ipsec transform-set MYTS esp-3des esp-md5-hmac
mode tunnel
!
crypto ipsec profile MY-IPSEC-PROFILE
set transform-set MYTS
set ikev2-profile MY-IKEV2-PROFILE
!
interface Tunnel0
ip address 192.168.100.4 255.255.255.0
tunnel source GigabitEthernet2
tunnel mode ipsec ipv4
tunnel destination 172.2.3.2
tunnel protection ipsec profile MY-IPSEC-PROFILE
!And verify the IKEv2 SA (Security Association) on CSR-2:
CSR-2#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 172.2.3.2/500 172.3.4.4/500 none/none READY
Encr: 3DES, PRF: SHA1, Hash: SHA96, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/615 sec
IPv6 Crypto IKEv2 SA And just to round it off, lets make sure we got dataplane connectivity as well:
CSR-1#ping 5.5.5.5 so loo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/2/5 msIn Summary:
My personal opinion is that SVTI is a much cleaner way of doing P2P S2S VPN’s. They offer a bunch of advantages compared to traditional configuration and administration. On top of that, newer code allows a mix of platforms to implement this (Fx. the Cisco ASA).
So i hope this has been a useful post for you. Let me know if you catch any errors or if you have any comments.
Thanks!
Merry Xmas.
/Kim