ISIS Authentication types (packet captures)
In this post i would like to highlight a couple of “features” of ISIS.
More specifically the authentication mechanism used and how it looks in the data plane.
I will do this by configuring a couple of routers and configure the 2 authentication types available. I will then look at packet captures taken from the link between them and illustrate how its used by the ISIS process.
The 2 types of Authentication are link-level authentication of the Hello messages used to establish an adjacency and the second type is the authentication used to authenticate the LSP’s (Link State Packet) themselves.
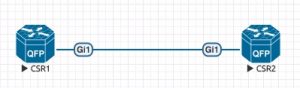
First off, here is the extremely simple topology, but its all thats required for this purpose:
Simple, right? 2 routers with 1 link between them on Gig1. They are both running ISIS level-2-only mode, which means they will only try and establish a L2 adjacency with their neighbors. Each router has a loopback interface, which is also advertised into ISIS.
First off, lets look at the relevant configuration of CSR-02 for the Link-level authentication:
key chain MY-CHAIN key 1 key-string WIPPIE ! interface GigabitEthernet1 ip address 10.1.2.2 255.255.255.0 ip router isis 1 negotiation auto no mop enabled no mop sysid isis authentication mode md5 isis authentication key-chain MY-CHAIN
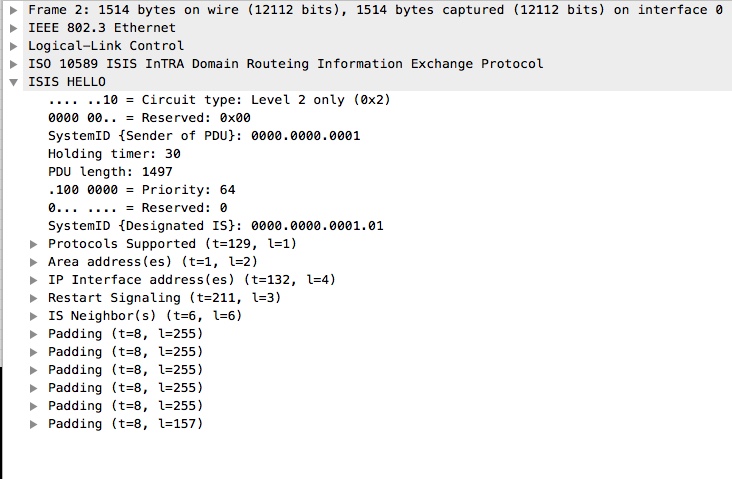
Without the same configuration on CSR-01, this is what we see in the data path (captured on CSR-02’s G1 interface):
And we also see that we dont have a full adjacency on CSR-01:
CSR-01#sh isis nei Tag 1: System Id Type Interface IP Address State Holdtime Circuit Id CSR-02 L2 Gi1 10.1.2.2 INIT 26 CSR-02.01
Lets apply the same authentication configuration on CSR-01 and see the result:
key chain MY-CHAIN key 1 key-string WIPPIE ! interface GigabitEthernet1 ip address 10.1.2.1 255.255.255.0 ip router isis 1 negotiation auto no mop enabled no mop sysid isis authentication mode md5 isis authentication key-chain MY-CHAIN
We now have a full adjacency:
CSR-01#sh isis neighbors Tag 1: System Id Type Interface IP Address State Holdtime Circuit Id CSR-02 L2 Gi1 10.1.2.2 UP 8 CSR-02.01
And we have routes from CSR-02:
CSR-01#sh ip route isis | beg Gate
Gateway of last resort is not set
2.0.0.0/32 is subnetted, 1 subnets
i L2 2.2.2.2 [115/20] via 10.1.2.2, 00:01:07, GigabitEthernet1
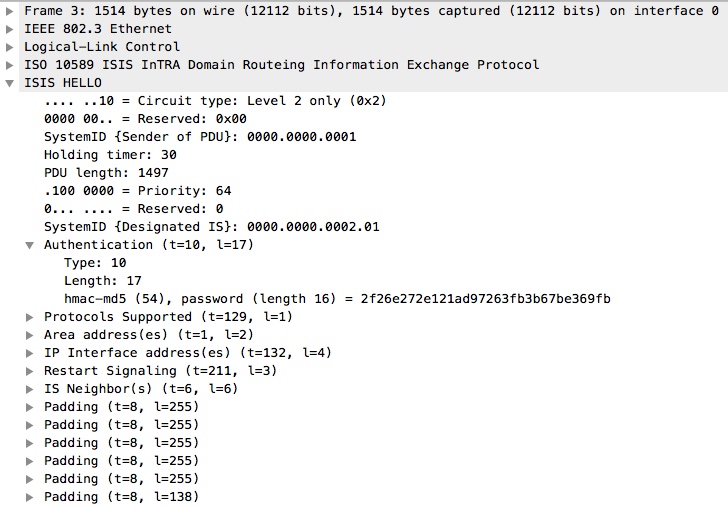
Now, this is what we now see from CSR-02’s perspective again:
The Link-level authentication is fairly easy to spot in no time, because you simply wont have a stable adjacency formed.
The second type is LSP authentication. Lets look at the configuration of CSR-02 for this type of authentication:
CSR-02#sh run | sec router isis ip router isis 1 ip router isis 1 router isis 1 net 49.0000.0000.0002.00 is-type level-2-only authentication mode text authentication key-chain MY-CHAIN
In this example, i have selected plain-text authentication, which i certainly dont recommend in production, but its great for our example.
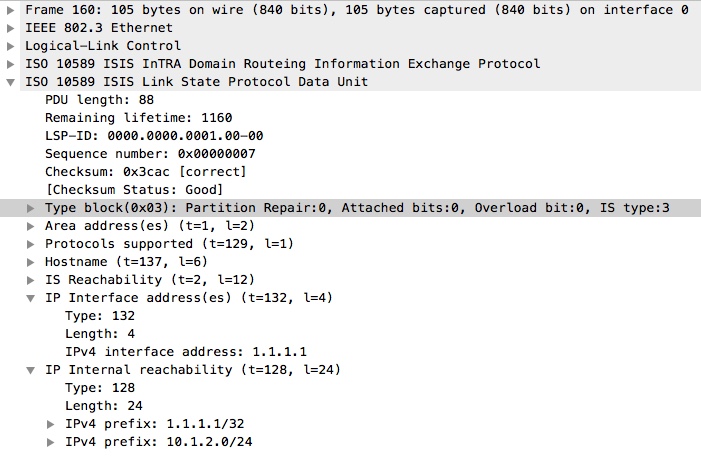
Again, this is what it looks like in the data packet (from CSR-01 to CSR-02) without authentication enabled on CSR-01:
As you can see, we have the LSP that contains CSR-01’s prefixes, but nowhere is authentication present in the packet.
Lets enable it on CSR-01 and see the result:
CSR-01#sh run | sec router isis ip router isis 1 ip router isis 1 router isis 1 net 49.0000.0000.0001.00 is-type level-2-only authentication mode text authentication key-chain MY-CHAIN
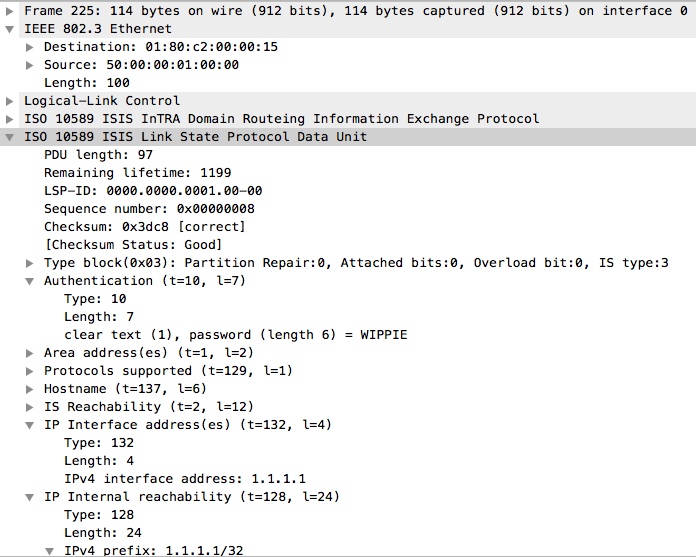
The result in the data packet:
Here we clearly have the authentication (with type = 10 (cleartext)) and we can see the password (WIPPIE) because we have selected cleartext.
The result is we a validated ISIS database on both routers.
Thats all folks, hope it helps to understand the difference between the 2 types of authentication in ISIS.
Take care!